1 监控应用程序启动退出模块加载卸载
1.1 控制台代码
#include "stdafx.h"
int main()
{
return 0;
}
1.2 双击启动进程,explorer.exe做的事情
首先,双击动作是explorer.exe产生的,在真实执行到Process Create之前,还有一大堆操作,这里就省略了,大致包括过程如下:
1、检查文件后缀
2、检查是否支持筛选器SmartScreen
3、找到文件后缀打开方式注册表
HKCR\exefile\shell\open\command
(默认) "%1" %*
IsolatedCommand "%1" %*
注意这里的"%1" %*,注册表中%表示取参数,%1是第一个参数,这里是即将被打开的exe全路径。如果我们把这个路径替换成别的,比如c:\windows\notepad.exe,这样用explorer.exe启动(双击或者右键菜单-打开)任何程序,都将打开记事本,一种简单的启动劫持方法
4、找到进程的ICON
5、启动进程
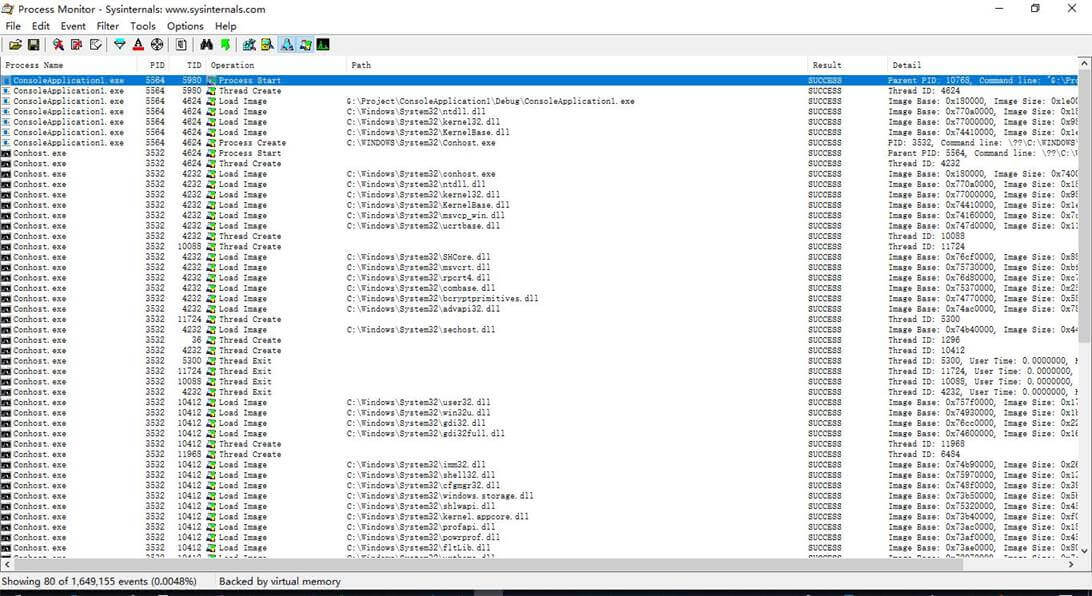
explorer.exe 10768 5980 Process Create G:\Project\ConsoleApplication1\Debug\ConsoleApplication1.exe SUCCESS PID: 5564, Command line: "G:\Project\ConsoleApplication1\Debug\ConsoleApplication1.exe"
ConsoleApplication1.exe 5564 5980 Process Start SUCCESS Parent PID: 10768, Command line: "G:\Project\ConsoleApplication1\Debug\ConsoleApplication1.exe" , Current directory: G:\Project\ConsoleApplication1\Debug\, Environment: ... // 相关环境变量
ConsoleApplication1.exe 5564 5980 Thread Create SUCCESS Thread ID: 4624
这里5980是explorer.exe的当前线程ID,5564是新进程的进程ID
1.3 镜像加载及卸载过程
ConsoleApplication1.exe 5564 5980 Process Start SUCCESS Parent PID: 10768, Command line: "G:\Project\ConsoleApplication1\Debug\ConsoleApplication1.exe" , Current directory: G:\Project\ConsoleApplication1\Debug\, Environment: ... // (环境变量作为参数一次性传递)
ConsoleApplication1.exe 5564 5980 Thread Create SUCCESS Thread ID: 4624
ConsoleApplication1.exe 5564 4624 Load Image G:\Project\ConsoleApplication1\Debug\ConsoleApplication1.exe SUCCESS Image Base: 0x180000, Image Size: 0x1e000
ConsoleApplication1.exe 5564 4624 Load Image C:\Windows\System32\ntdll.dll SUCCESS Image Base: 0x770a0000, Image Size: 0x18f000
ConsoleApplication1.exe 5564 4624 Load Image C:\Windows\System32\kernel32.dll SUCCESS Image Base: 0x77000000, Image Size: 0x98000
ConsoleApplication1.exe 5564 4624 Load Image C:\Windows\System32\KernelBase.dll SUCCESS Image Base: 0x74410000, Image Size: 0x1e6000
ConsoleApplication1.exe 5564 4624 Process Create C:\WINDOWS\System32\Conhost.exe SUCCESS PID: 3532, Command line: \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1
Conhost.exe 3532 4624 Process Start SUCCESS Parent PID: 5564, Command line: \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1, Current directory: C:\WINDOWS, Environment: ... // (环境变量作为参数一次性传递)
Conhost.exe 3532 4624 Thread Create SUCCESS Thread ID: 4232
Conhost.exe 3532 4232 Load Image C:\Windows\System32\conhost.exe SUCCESS Image Base: 0x180000, Image Size: 0x74000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\ntdll.dll SUCCESS Image Base: 0x770a0000, Image Size: 0x18f000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\kernel32.dll SUCCESS Image Base: 0x77000000, Image Size: 0x98000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\KernelBase.dll SUCCESS Image Base: 0x74410000, Image Size: 0x1e6000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\msvcp_win.dll SUCCESS Image Base: 0x74160000, Image Size: 0x7d000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\ucrtbase.dll SUCCESS Image Base: 0x747d0000, Image Size: 0x11e000
Conhost.exe 3532 4232 Thread Create SUCCESS Thread ID: 10088
Conhost.exe 3532 10088 Thread Create SUCCESS Thread ID: 11724
Conhost.exe 3532 4232 Load Image C:\Windows\System32\SHCore.dll SUCCESS Image Base: 0x76cf0000, Image Size: 0x88000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\msvcrt.dll SUCCESS Image Base: 0x75730000, Image Size: 0xbf000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\rpcrt4.dll SUCCESS Image Base: 0x76d80000, Image Size: 0xc7000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\combase.dll SUCCESS Image Base: 0x75370000, Image Size: 0x25c000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\bcryptprimitives.dll SUCCESS Image Base: 0x74770000, Image Size: 0x58000
Conhost.exe 3532 4232 Load Image C:\Windows\System32\advapi32.dll SUCCESS Image Base: 0x74ac0000, Image Size: 0x78000
Conhost.exe 3532 11724 Thread Create SUCCESS Thread ID: 5300
Conhost.exe 3532 4232 Load Image C:\Windows\System32\sechost.dll SUCCESS Image Base: 0x74b40000, Image Size: 0x44000
Conhost.exe 3532 36 Thread Create SUCCESS Thread ID: 1296
Conhost.exe 3532 4232 Thread Create SUCCESS Thread ID: 10412
Conhost.exe 3532 5300 Thread Exit SUCCESS Thread ID: 5300, User Time: 0.0000000, Kernel Time: 0.0000000
Conhost.exe 3532 11724 Thread Exit SUCCESS Thread ID: 11724, User Time: 0.0000000, Kernel Time: 0.0000000
Conhost.exe 3532 10088 Thread Exit SUCCESS Thread ID: 10088, User Time: 0.0000000, Kernel Time: 0.0000000
Conhost.exe 3532 4232 Thread Exit SUCCESS Thread ID: 4232, User Time: 0.0000000, Kernel Time: 0.0156250
Conhost.exe 3532 10412 Load Image C:\Windows\System32\user32.dll SUCCESS Image Base: 0x757f0000, Image Size: 0x174000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\win32u.dll SUCCESS Image Base: 0x74930000, Image Size: 0x1b000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\gdi32.dll SUCCESS Image Base: 0x76cc0000, Image Size: 0x22000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\gdi32full.dll SUCCESS Image Base: 0x74600000, Image Size: 0x167000
Conhost.exe 3532 10412 Thread Create SUCCESS Thread ID: 11968
Conhost.exe 3532 11968 Thread Create SUCCESS Thread ID: 6484
Conhost.exe 3532 10412 Load Image C:\Windows\System32\imm32.dll SUCCESS Image Base: 0x74b90000, Image Size: 0x26000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\shell32.dll SUCCESS Image Base: 0x75970000, Image Size: 0x134a000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\cfgmgr32.dll SUCCESS Image Base: 0x748f0000, Image Size: 0x39000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\windows.storage.dll SUCCESS Image Base: 0x73b50000, Image Size: 0x5ba000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\shlwapi.dll SUCCESS Image Base: 0x75320000, Image Size: 0x45000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\kernel.appcore.dll SUCCESS Image Base: 0x73b40000, Image Size: 0xf000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\profapi.dll SUCCESS Image Base: 0x73ac0000, Image Size: 0x18000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\powrprof.dll SUCCESS Image Base: 0x73af0000, Image Size: 0x45000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\fltLib.dll SUCCESS Image Base: 0x73ae0000, Image Size: 0x8000
Conhost.exe 3532 10412 Load Image C:\Windows\System32\uxtheme.dll SUCCESS Image Base: 0x72070000, Image Size: 0x7c000
Conhost.exe 3532 10412 Thread Create SUCCESS Thread ID: 7188
Conhost.exe 3532 10412 Thread Create SUCCESS Thread ID: 9968
Conhost.exe 3532 9968 Load Image C:\Windows\System32\msctf.dll SUCCESS Image Base: 0x76eb0000, Image Size: 0x143000
Conhost.exe 3532 9968 Load Image C:\Windows\System32\oleaut32.dll SUCCESS Image Base: 0x751f0000, Image Size: 0x96000
Conhost.exe 3532 9968 Load Image C:\Windows\System32\dwmapi.dll SUCCESS Image Base: 0x723d0000, Image Size: 0x23000
Conhost.exe 3532 9968 Load Image C:\Windows\WinSxS\x86_microsoft.windows.common-controls_6595b64144ccf1df_6.0.17134.523_none_42edd4b044e3535c\comctl32.dll SUCCESS Image Base: 0x67920000, Image Size: 0x204000
Conhost.exe 3532 9968 Load Image C:\Windows\System32\TextInputFramework.dll SUCCESS Image Base: 0x6d360000, Image Size: 0x7d000
Conhost.exe 3532 9968 Load Image C:\Windows\System32\CoreMessaging.dll SUCCESS Image Base: 0x71ad0000, Image Size: 0xa6000
Conhost.exe 3532 11968 Load Image C:\Windows\System32\CoreUIComponents.dll SUCCESS Image Base: 0x6cff0000, Image Size: 0x25d000
Conhost.exe 3532 11968 Thread Create SUCCESS Thread ID: 8848
Conhost.exe 3532 6484 Load Image C:\Windows\System32\ntmarta.dll SUCCESS Image Base: 0x72de0000, Image Size: 0x29000
Conhost.exe 3532 8848 Load Image C:\Windows\System32\WinTypes.dll SUCCESS Image Base: 0x70030000, Image Size: 0xd6000
Conhost.exe 3532 11968 Load Image C:\Windows\System32\WinTypes.dll SUCCESS Image Base: 0x44a0000, Image Size: 0xd6000
Conhost.exe 3532 9968 Load Image C:\Windows\System32\clbcatq.dll SUCCESS Image Base: 0x75290000, Image Size: 0x83000
ConsoleApplication1.exe 5564 4624 Thread Create SUCCESS Thread ID: 952
ConsoleApplication1.exe 5564 4624 Load Image C:\Windows\System32\vcruntime140d.dll SUCCESS Image Base: 0x634c0000, Image Size: 0x1c000
ConsoleApplication1.exe 5564 4624 Load Image C:\Windows\System32\ucrtbased.dll SUCCESS Image Base: 0xff00000, Image Size: 0x171000
ConsoleApplication1.exe 5564 4624 Load Image C:\Windows\System32\kernel.appcore.dll SUCCESS Image Base: 0x73b40000, Image Size: 0xf000
ConsoleApplication1.exe 5564 4624 Load Image C:\Windows\System32\msvcrt.dll SUCCESS Image Base: 0x75730000, Image Size: 0xbf000
ConsoleApplication1.exe 5564 4624 Load Image C:\Windows\System32\rpcrt4.dll SUCCESS Image Base: 0x76d80000, Image Size: 0xc7000
ConsoleApplication1.exe 5564 4624 Thread Exit SUCCESS Thread ID: 4624, User Time: 0.0312500, Kernel Time: 0.0000000
ConsoleApplication1.exe 5564 952 Thread Exit SUCCESS Thread ID: 952, User Time: 0.0000000, Kernel Time: 0.0000000
ConsoleApplication1.exe 5564 952 Process Exit SUCCESS Exit Status: 0, User Time: 0.0312500 seconds, Kernel Time: 0.0000000 seconds, Private Bytes: 524,288, Peak Private Bytes: 524,288, Working Set: 2,306,048, Peak Working Set: 2,306,048
Conhost.exe 3532 11968 Thread Exit SUCCESS Thread ID: 11968, User Time: 0.0000000, Kernel Time: 0.0000000
Conhost.exe 3532 7188 Thread Exit SUCCESS Thread ID: 7188, User Time: 0.0000000, Kernel Time: 0.0000000
Conhost.exe 3532 9968 Thread Exit SUCCESS Thread ID: 9968, User Time: 0.0156250, Kernel Time: 0.0468750
Conhost.exe 3532 10412 Thread Exit SUCCESS Thread ID: 10412, User Time: 0.0000000, Kernel Time: 0.0156250
Conhost.exe 3532 6484 Thread Exit SUCCESS Thread ID: 6484, User Time: 0.0000000, Kernel Time: 0.0000000
Conhost.exe 3532 8848 Thread Exit SUCCESS Thread ID: 8848, User Time: 0.0000000, Kernel Time: 0.0000000
Conhost.exe 3532 1296 Thread Exit SUCCESS Thread ID: 1296, User Time: 0.0000000, Kernel Time: 0.0000000
Conhost.exe 3532 7188 Process Exit SUCCESS Exit Status: 0, User Time: 0.0156250 seconds, Kernel Time: 0.0781250 seconds, Private Bytes: 5,390,336, Peak Private Bytes: 5,828,608, Working Set: 13,242,368, Peak Working Set: 13,320,192
常规的加载模块,需要了解清楚,以便做病毒分析时,能迅速感知到异常模块加载。模块启动卸载过程依次:
ConsoleApplication1.exe:控制台主程序
ConsoleApplication1!ntdll.dll:内核打交道相关,比如LdrLoadDll
ConsoleApplication1!kernel32.dll:基本组件外壳,比如CopyFile、CreateProcess等,配合kernelBase.dll
ConsoleApplication1!KernelBase.dll:基本组件,比如CopyFile、CreateProcess等
Conhost.exe:控制台宿主程序,用于界面部分展示
Conhost!ntdll.dll
Conhost!kernel32.dll
Conhost!KernelBase.dll
Conhost!msvcp_win.dll:标准库std stream相关
Conhost!ucrtbase.dll:C运行时库,比如:strncpy
Conhost!SHCore.dll:Shell核心库,比如:CommandLineToArgv、SHDeleteKey
Conhost!msvcrt.dll:微软实现的C运行时库,比如:wprintf
Conhost!rpcrt4.dll:远程程序调用,用于对网络连接,比如:RpcServerListen
Conhost!combase.dll:COM组件接口,比如:CoInitializeEx
Conhost!bcryptprimitives.dll:大概是处理加密相关的,比如:GetAsymmetricEncryptionInterface
Conhost!advapi32.dll:跟核心组件exe交互的dll,以及一些事件日志性能监控等,比如:OpenSCManager、WmiQueryGuidInformation
Conhost!sechost.dll:服务相关,比如:StartService
Conhost!user32.dll:用户交互相关,比如:CreateWindowEx
Conhost!win32u.dll:内核界面交互相关,比如:NtGdiCreateSolidBrush
Conhost!gdi32.dll:图形绘制库,比如:CreateDC
Conhost!gdi32full.dll:图形绘制库,比如:CreateDC
Conhost!imm32.dll:输入法相关
Conhost!shell32.dll:Shell相关,比如:SHCreateDirectoryEx
Conhost!cfgmgr32.dll:设备交互相关,比如:CM_Setup_DevNode
Conhost!windows.storage.dll:WSS存储服务,大概是为了集群,例如:STORAGE_SHFileOperation
Conhost!kernel.appcore.dll:大概是Win10应用商店之类的程序要使用的
Conhost!profapi.dll:不晓得
Conhost!powrprof.dll:电源相关,例如:DevicePowerOpen
Conhost!fltLib.dll:过滤驱动调用相关,例如:FilterFindFirst
Conhost!uxtheme.dll:主题相关,例如:DrawThemeBackground
Conhost!msctf.dll:好像是系统输入法相关,可能是触屏输入法,例如:CtfNotifyIME
Conhost!oleaut32.dll:OLE组件相关,例如:OleIconToCursor
Conhost!dwmapi.dll:vista之后界面相关,毛玻璃、3d动画、高分辨率等,例如:DwmEnableComposition
Conhost!comctl32.dll:通用控件,例如:ImageList_Create
Conhost!TextInputFramework.dll:文本输入相关,例如:TextInputClientCreate
Conhost!CoreMessaging.dll:Win10下,处理系统组件交互的,例如:CoreUICreateEx
Conhost!CoreUIComponents.dll:可能也是Win10下处理UI组件相关,例如:CoreUIClientCreate
Conhost!ntmarta.dll:访问控制的,例如:AccConvertAccessToSD
Conhost!WinTypes.dll:UWP相关,例如:RoParseTypeName
Conhost!clbcatq.dll:COM+配置相关,例如:ComPlusMigrate
ConsoleApplication1!vcruntime140d.dll:VC运行时库,例如:__vcrt_GetModuleFileName
ConsoleApplication1!ucrtbased.dll
ConsoleApplication1!kernel.appcore.dll
ConsoleApplication1!msvcrt.dll
ConsoleApplication1!rpcrt4.dll
2、不同维度的性能分析工具
Procmon用于性能分析,主要是它的事件跟踪和统计特性,特别是统计特性。另外,它同时统计的是应用层和驱动层的事件信息,所以可以比较直观的观测到上下层谁的影响。
在Tools中,有几种统计方法:
(1)Process Active Summary:总图,有关进程的CPU占用情况、File Events总数及历史记录曲线、File I/O字节数、注册表Events总数及历史记录曲线、Network Events总数及历史记录曲线、内存使用情况。双击曲线中某个点,会自动跳转到对应的监控事件,这样,任何有波动的曲线,都能找到是由哪个event引起的,进一步查看回溯栈,可以找到最终影响性能的点
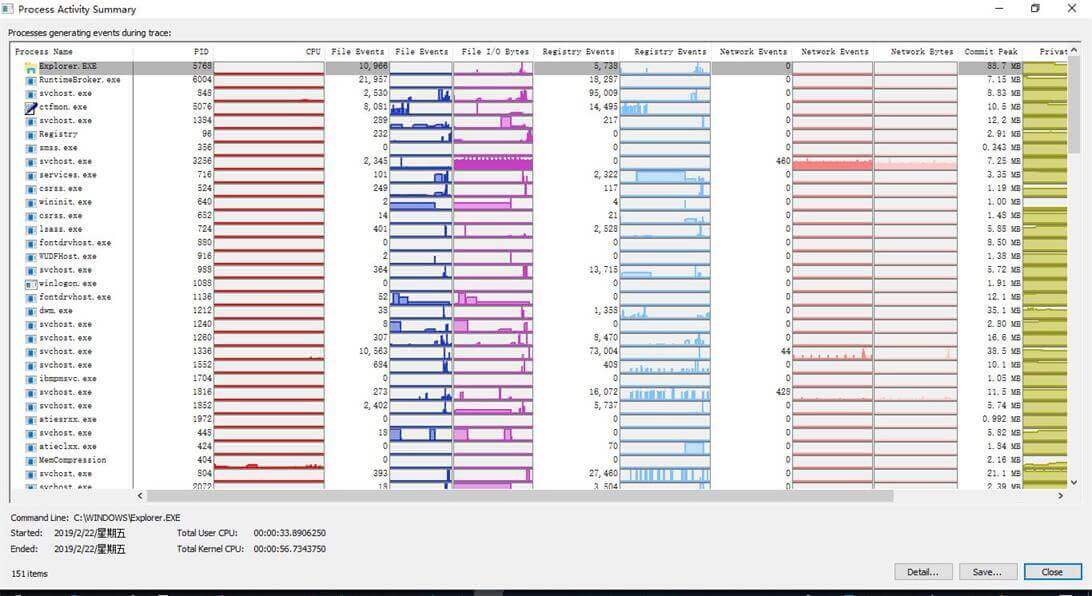
比如发现svchost大量文件IO,双击曲线中峰值点,发现是迅雷搞事情
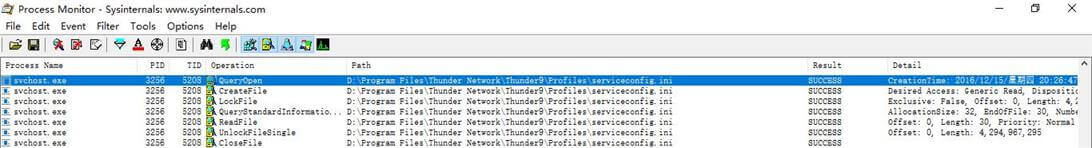
(2)File Summary:文件操作情况,可以非常灵活的按照过滤,去选择自己关心的事件组合。按照文件操作耗时的排序,也方便的查看到性能影响点
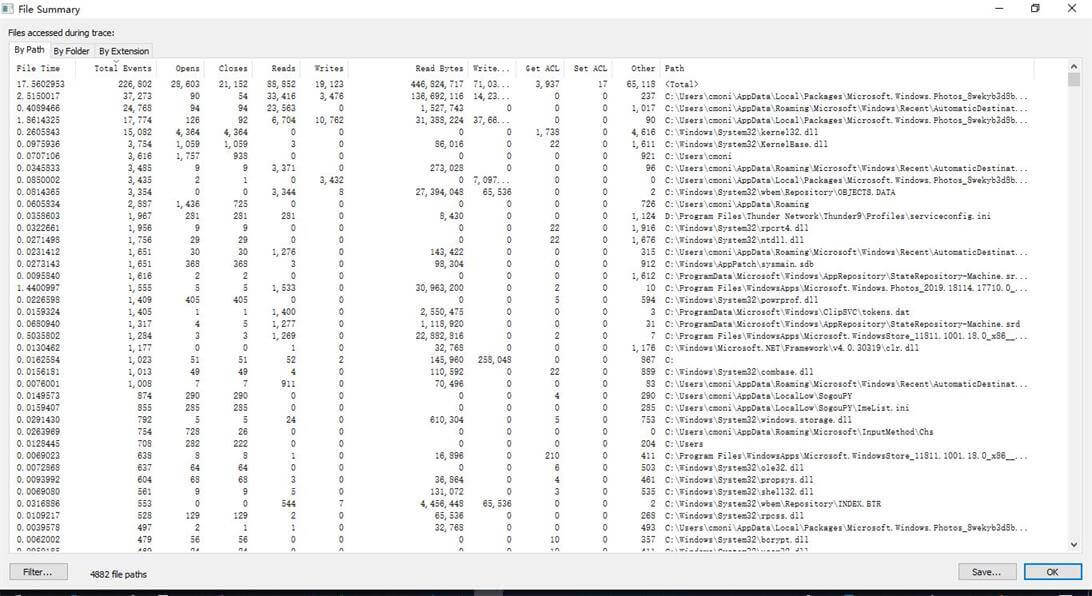
图中可以看出,文件操作性能影响最大的,是Microsoft.photos.exe在大量的读写。当然,这个不能表达全部的性能影响,有时候,我们需要看的是单位时间的影响情况,这个就需要我们自己除时间运算,取平均看一下。
(3)Register Summary:注册表操作性能影响点,参考文件的
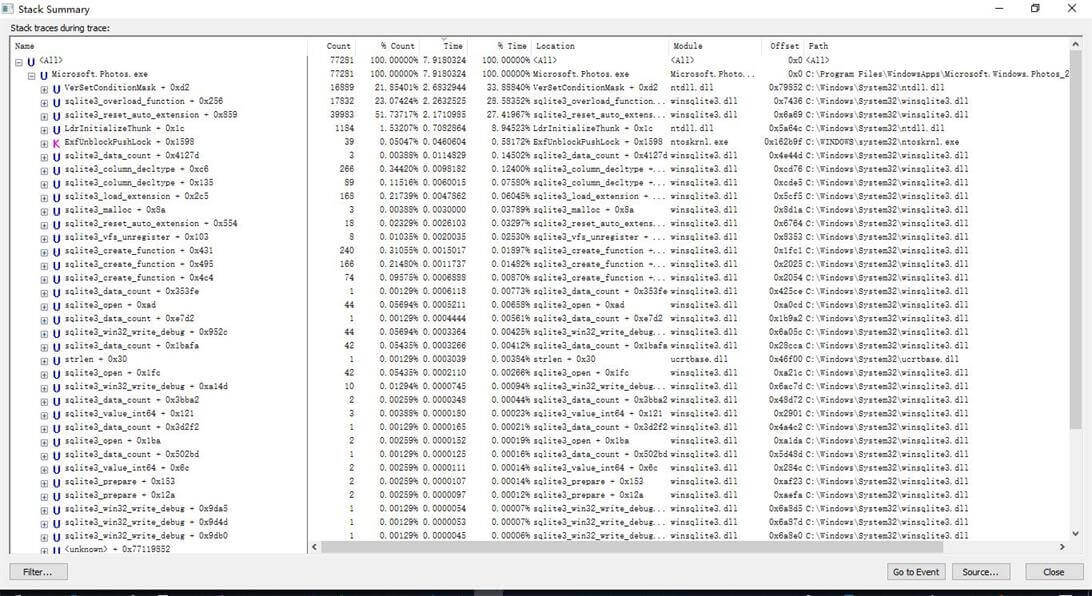
(4)Stack Summary:线程栈的性能影响,这个可以更加详细看到哪些API调用比较多,比较耗时等
(5)Network Summary:网络连接统计情况,包括字节数,这里主要关注的是流量
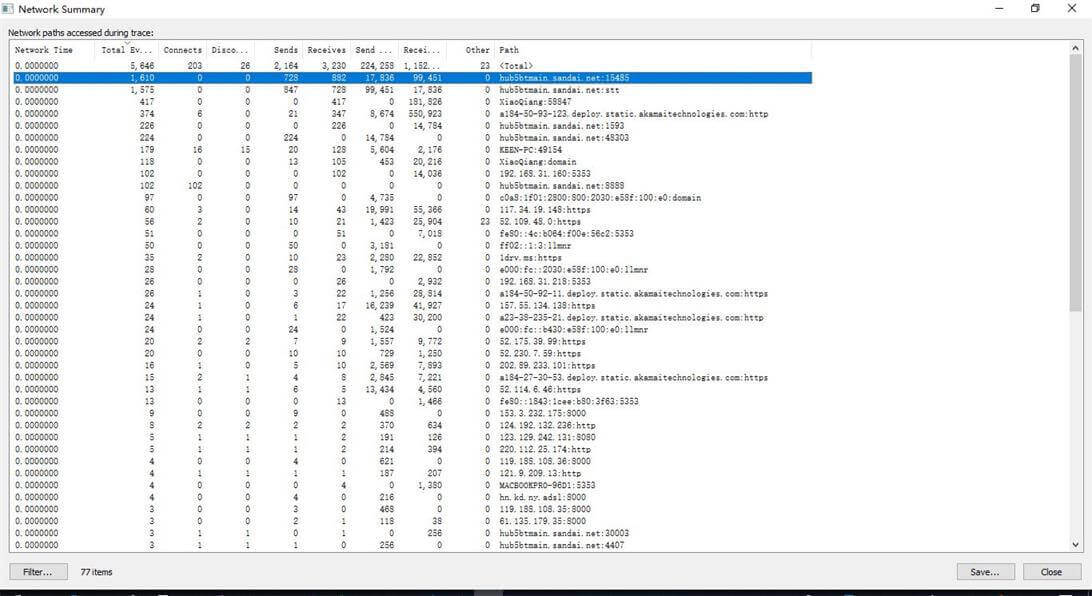
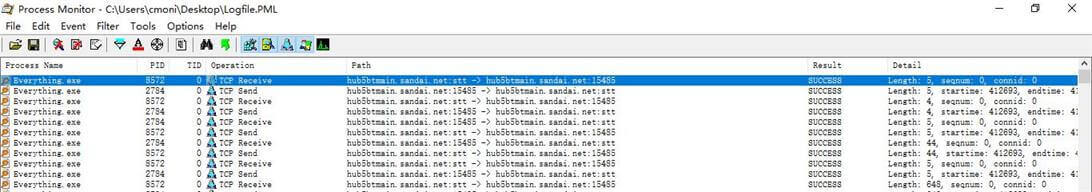
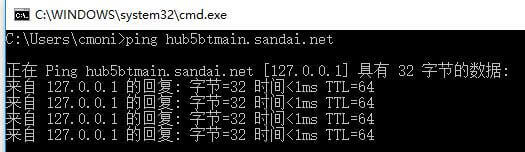
可以看到everything.exe在进行大量的数据包传输,仔细ping一下这个域名hub5btmain.sandai.net,发现是一个本地连接
(6)Cross Reference Summary:查看文件被交叉引用占用(读或者写操作)
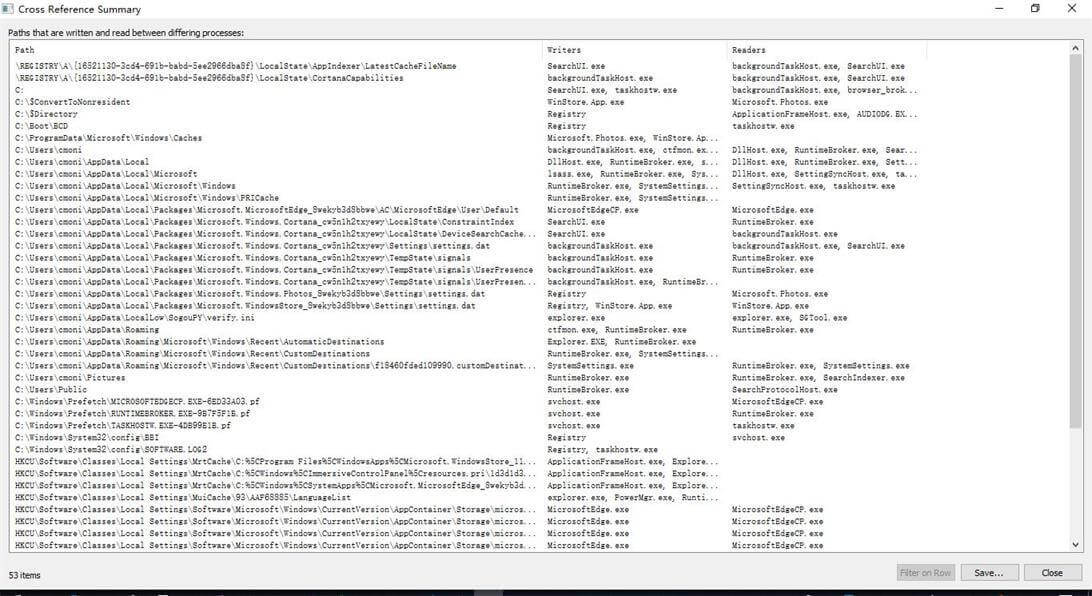
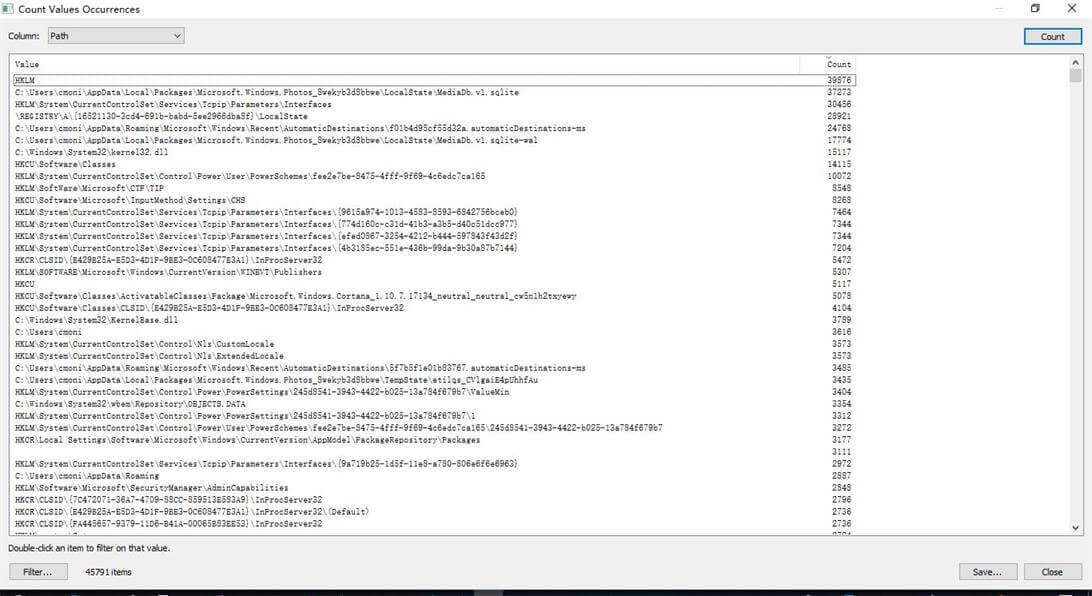
(7)Count Occurrences:查看某种关键字的事件统计量,比如某进程事件总数、path总数
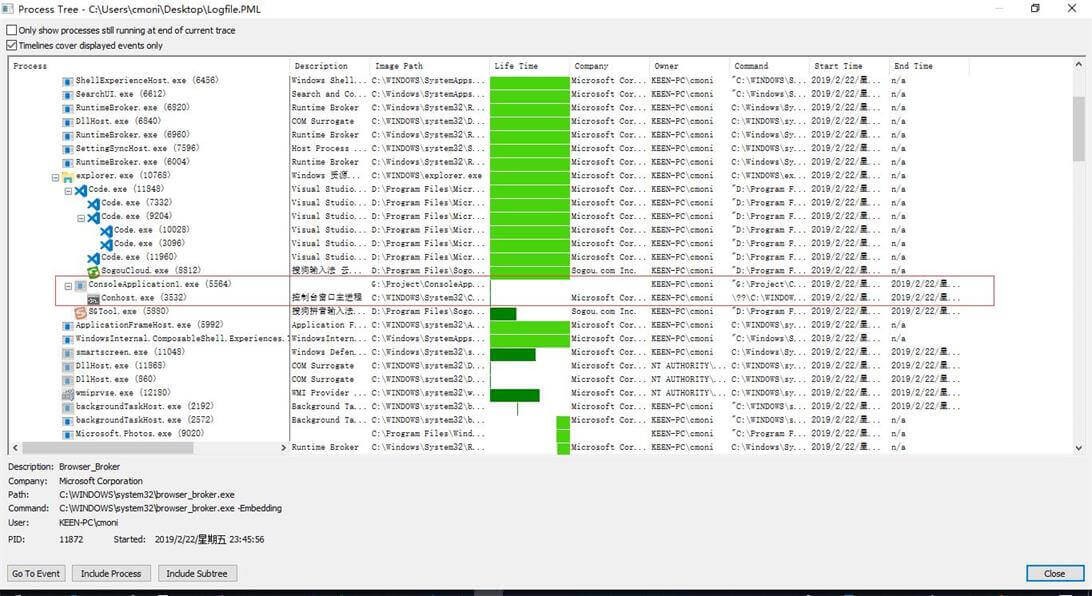
3、查看进程关系链
利用Procmon中的Tools里的Process Tree,可以方便查看到整个运行中的进程链(还可以包括退出的进程,这个是区别于Process Explorer)。通过这里的进程树,可以方便查看进程关系链,然后将整个关系链加入到Filter中
3 Procmon原理
运行时,会释放PROCMONX24.SYS等驱动文件到system32目录,监控信息本质是由驱动+ETW架构辅助完成
详细技术框架,未完待续





